Like antivirus software, vulnerability scans rely on a database of known weaknesses.
That’s why websites like VirusTotal exist, to give cyber practitioners a chance to see whether a malware sample is detected by multiple virus scanning engines, but this concept hasn’t existed in the vulnerability management space.
The benefits of using multiple scanning engines
Generally speaking, vulnerability scanners aim to produce checks for as many vulnerabilities as possible. However, the number of vulnerabilities discovered year on year is now so high, reaching nearly 30,000 a year, or 80 a day, that it’s impossible for a single scanning engine to keep up with them all.
As a result, even the very best, industry-leading leading scanners will struggle to check for every known vulnerability out there, and often they will favour certain sets of software known to be used by their customers.
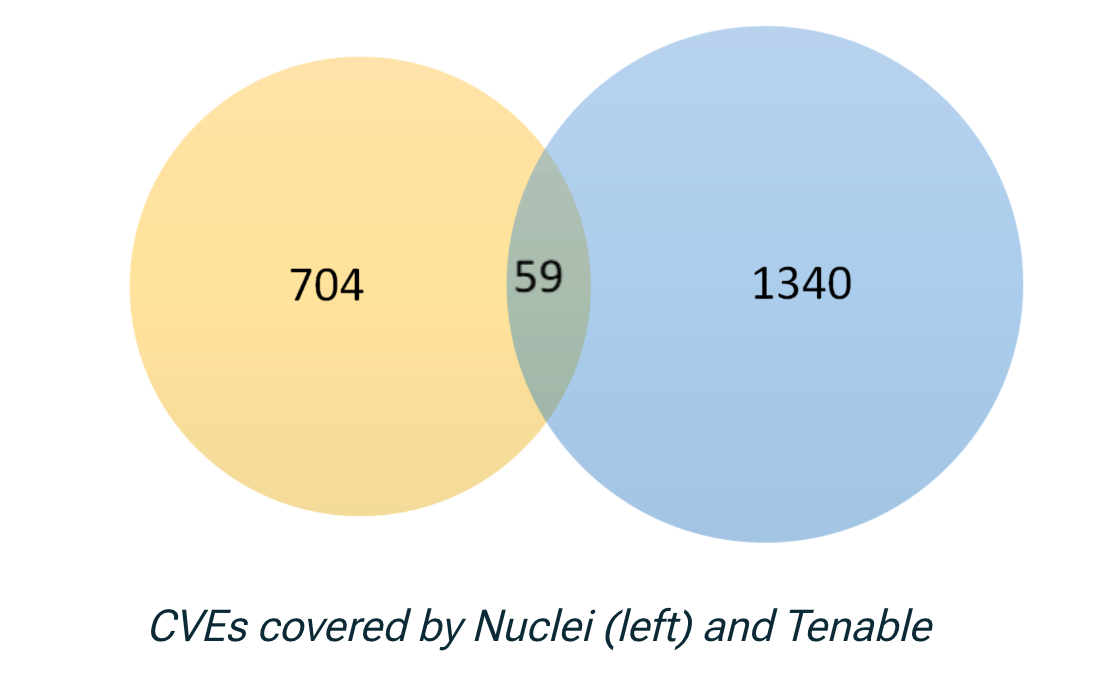
For example, Intruder’s analysis from early 2023 which compared Tenable’s Nessus and OpenVAS showed significant differences in coverage between scanners, with one being generally stronger in commercial software, and the other favouring open source:
“Tenable checks for 12,015 CVEs which OpenVAS does not check for and OpenVAS checks for 6,749 CVEs which Tenable does not check for.”
Scanning engine vendors also take other factors into consideration, like whether a vulnerability has been exploited in the wild, or whether it’s in software products which are very widely used. But even though your chosen scanner may be making sensible decisions on which vulnerabilities to write checks for there may still be gaps in coverage for your estate.
So it’s a harsh reality that one day you may find out that you’ve been compromised via an attack vector which your vulnerability scanner simply doesn’t have a check for.
This raises significant questions for those looking to protect their digital estates, not only which scanner they should choose. But whether one scanner is even enough?
The multi-scanning engine approach
It’s clear that having several complementary scanners would improve coverage by finding more vulnerabilities, and discovering more about what your attack surface looks like. But operating multiple scanning systems would be too much for most organisations to afford, both in budget and time constraints.
That’s why the team at Intruder, a leading Attack Surface Management vendor, decided from the start to incorporate multiple scanning engines, offering customers the widest breadth of checks, while streamlining budget and time constraints by providing them in a single platform.
Most recently, Intruder has added Nuclei to its suite of vulnerability scanning engines, enhancing its ability to manage and secure attack surfaces.
With over 3,000 additional checks in this initial release, Intruder can offer much broader and deeper coverage and discovery capabilities that can’t be matched by using a single vulnerability scanner alone.
What is Nuclei?
Nuclei is an open-source vulnerability scanning engine, similar to OpenVAS, which is fast, extensible, and covers a wide range of weaknesses. It’s become increasingly popular with bug bounty hunters, penetration testers and researchers who want to produce repeatable checks for serious weaknesses.
These experts, working with the Nuclei development team at ProjectDiscovery, combine their knowledge and insights about cutting-edge weaknesses to produce checks extremely fast – which makes scanning as soon as possible after a vulnerability is discovered.
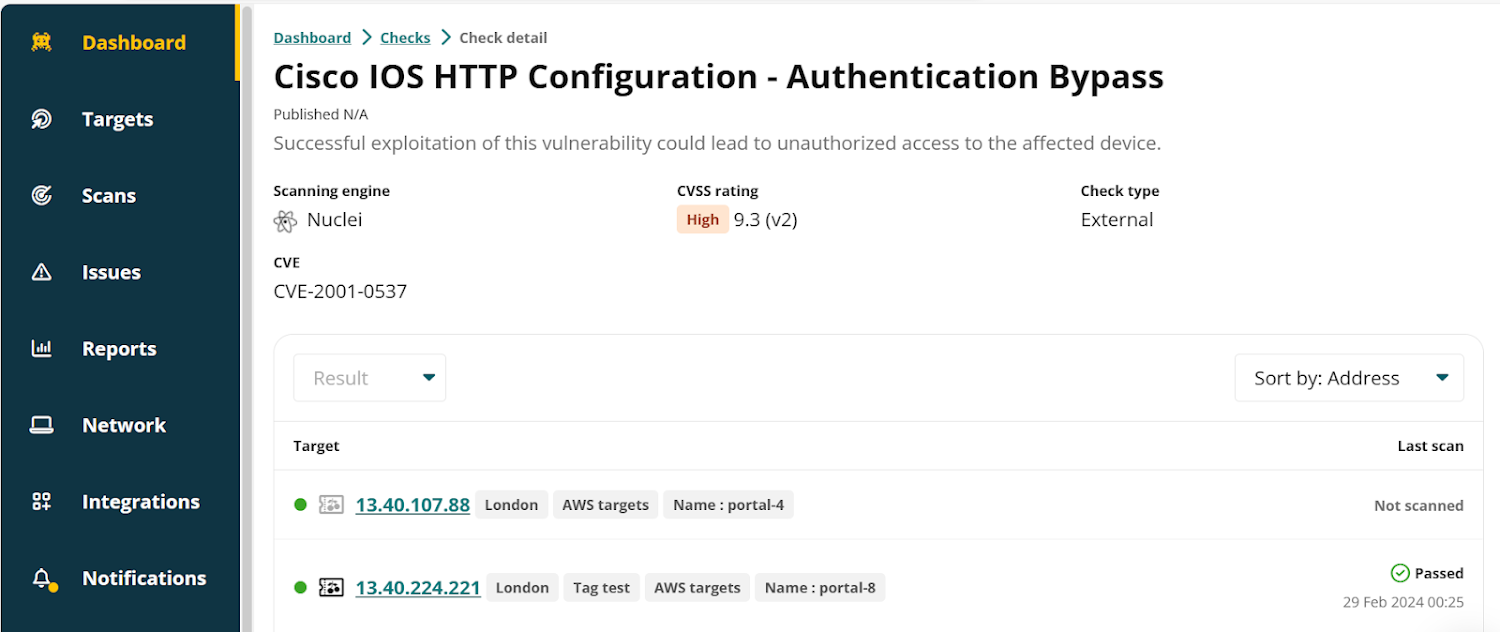 |
| An example of a Nuclei check in the Intruder platform |
What does Nuclei add to Intruder?
By integrating Nuclei as a scanning engine, Intruder further enhances its vulnerability management platform capabilities to check and secure attack surfaces more effectively.
This includes expanded detection of exposures like login panels that should not be exposed to the internet, and increasing the range of checks for known vulnerabilities in commonly exposed services.
Nuclei augments Intruder’s existing scanning engines, such as Tenable and OpenVAS, by providing a deeper and broader view of your attack surface, thus enabling better protection by uncovering risks that would remain undetected by a single scanning engine.
Visualize and minimize your exposure with Intruder
The size of your attack surface, and how well it’s managed, is closely tied to your risk of opportunistic attackers exploiting your systems. The less you expose, and the more hardened the services you expose are, the harder it is for an attacker to exploit a weakness.
You can reduce your attack surface by continuously monitoring for changes with an automated vulnerability management tool like Intruder.
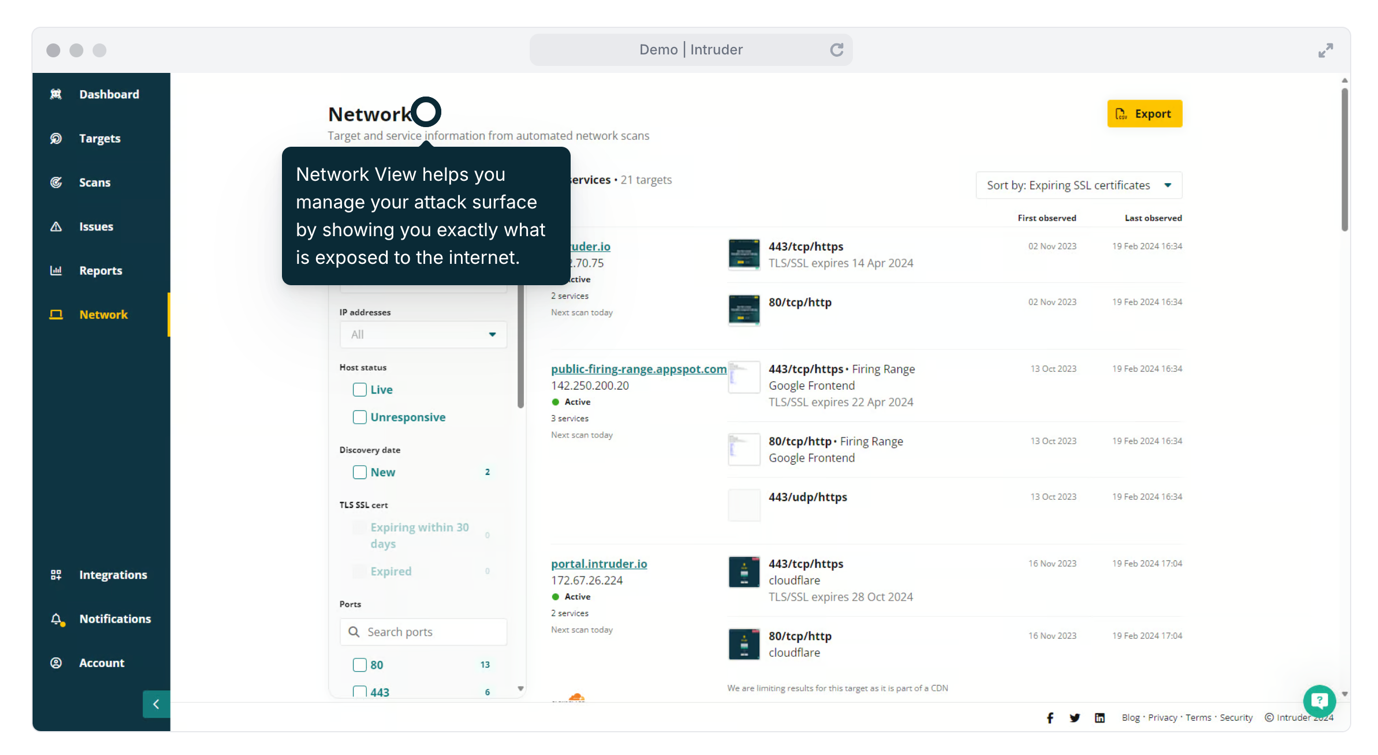 |
| A screenshot of Intruder’s attack surface management dashboard. |
Intruder’s platform allows you to:
- Discover assets: when new cloud services are spun up and exposed to the internet, Intruder kicks off a scan to find any vulnerabilities so you can fix them faster.
- Know what’s exposed: get complete visibility of your network perimeter, track active and unresponsive targets, identify changes, monitor expiring certificates, and see any ports, services or protocols that shouldn’t be exposed to the internet.
- Detect more: Intruder uses multiple scanners to identify vulnerabilities and exposures across your attack surface giving you the greatest visibility.
- Focus on the big issues: see results prioritized based on context, so you can focus on the most pressing problems without wasting time sifting through the noise.